

Nasty RAT - Quick Malware Analysis
SHA256: 29c5d95091225f205e9bac473b951244fc3bfec0ca1298008b04cf2f4035d136
File: Client.exe
Unknown base64 strings, most likely encrypted that could be useful upon further analysis:
8BpGK/82DsDIq8mBt2REuGv/+SHxF77bgz7h4JdTt00hiFDJGptzrwyY2TEJhYFBsdcuYtIfrkLPCHgGpGpFXSiKTVVF1NHqwopiSGZYtmw=
T+t+jwQAhhrS3XJ575fE5A==
PulWNjqvE3Wvu075wEpRE2LwDmfaJferrKl2dcUCJpUqS42V2bASa0FimbfiGl0+AZmidkiQfD7Z4GpweB4ZsQ==TVVF1NHqwopiSGZYtmw=
OQGUDxlMmUUo2dgGT1x7pn0J6d5/C2uIAC5QWErE2XAdYnGzISJn1PzEMMbM7OcsXsKZf0ggDO7KCQ9Gq5OckTWQcfMZTvloq7xlJyKjx6s=
vbnPNNwt+yzIgFMANpl0g7HrLykYm6Ku8T3dt0AZq1ZseQdJrK0OHddwnHC5pawQo2mIBGUeola7S2Ow+8gajg==cfMZTvloq7xlJyKjx6s=
7TF0Q9isBKyaImr7BwdnOhR5jn3AblDhcJxTpPNniQEM2KOKw11LdDA6LYf01f2HUpHBR0ZhnETnl1saAg9Qqw==
t0vYmV001ORHFPgdzEqftMBtUX1HrrhajCkKMdJZI0fLqa+5uoESLUMpWXOCBwwwV9t7LpSDtD00pZLJrscx4g==
OQGUDxlMmUUo2dgGT1x7pn0J6d5/C2uIAC5QWErE2XAdYnGzISJn1PzEMMbM7OcsXsKZf0ggDO7KCQ9Gq5OckTWQcfMZTvloq7xlJyKjx6s=
T+t+jwQAhhrS3XJ575fE5A==
ulWNjqvE3Wvu075wEpRE2LwDmfaJferrKl2dcUCJpUqS42V2bASa0FimbfiGl0+AZmidkiQfD7Z4GpweB4ZsQ==
lnkX+EZGrjZydIryWDc0BSvStegj2JcVA6ZXBchmG4vh8b5xfv9ZRlECnLxmjK09grOd4/GIV12N4uCe4N1n8w==
UdI9DC2j0gvHny5C2F4I
lnkX+EZGrjZydIryWDc0BSvStegj2JcVA6ZXBchmG4vh8b5xfv9ZRlECnLxmjK09grOd4/GIV12N4uCe4N1n8w==
8BpGK/82DsDIq8mBt2REuGv/+SHxF77bgz7h4JdTt00hiFDJGptzrwyY2TEJhYFBsdcuYtIfrkLPCHgGpGpFXSiKTVVF1NHqwopiSGZYtmw=
T+t+jwQAhhrS3XJ575fE5A==
/I087GCyAQK5zS55ac4jFd9m8Z73l56RVAYKDjk4V/TZS8ijF29RssENL2o/CtevRgrqaK/jOR7/TjeRWZVaQA==
PulWNjqvE3Wvu075wEpRE2LwDmfaJferrKl2dcUCJpUqS42V2bASa0FimbfiGl0+AZmidkiQfD7Z4GpweB4ZsQ=="
t0vYmV001ORHFPgdzEqftMBtUX1HrrhajCkKMdJZI0fLqa+5uoESLUMpWXOCBwwwV9t7LpSDtD00pZLJrscx4g==
OQGUDxlMmUUo2dgGT1x7pn0J6d5/C2uIAC5QWErE2XAdYnGzISJn1PzEMMbM7OcsXsKZf0ggDO7KCQ9Gq5OckTWQcfMZTvloq7xlJyKjx6s=
r6XrP+21/yzf1a2otFFlO3XhBx1Dkudy8HdLAir7U9R9HYVz4AgXjQW1lN6OGhauQfjWXA/c5IJlT0QnLEVJELsVe3cV7JfKmNRagwdKgyE=
UdI9DC2j0gvHny5C2F4
vbnPNNwt+yzIgFMANpl0g7HrLykYm6Ku8T3dt0AZq1ZseQdJrK0OHddwnHC5pawQo2mIBGUeola7S2Ow+8gajg==
7TF0Q9isBKyaImr7BwdnOhR5jn3AblDhcJxTpPNniQEM2KOKw11LdDA6LYf01f2HUpHBR0ZhnETnl1saAg9Qqw==
The sample was not executed. Basic dynamic analysis indicated that the malware would require a genuine internet connection, and my current lab environment is designed to use an isolated network served by InetSIM. It may be necessary to execute this malware to more easily determine network based indicators. As discussed below, there are many indications that the malware will communicate with an external IP address, but it appears that this address(es) or URLs are decrypted at runtime.
Decompiling the sample I was able to assume the general behavior without dynamic analysis. The sample contains descriptive class and method names as well as descriptive error/debugging messages.
The first operation the malware performs is comprehensive fingerprinting of the host. This includes processor, motherboard manufacturer, connected removeable storage, network storage, webcams and audio recording devices. The malware also queries for installed anti-virus products and operating system information.
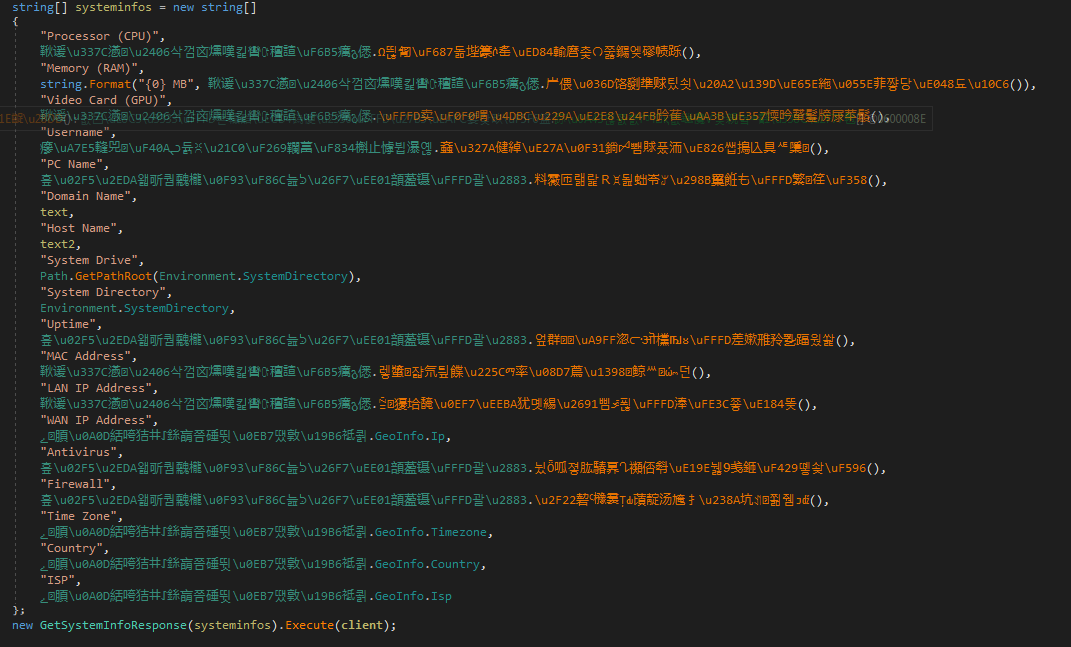
In addition to the hardware fingerprinting, the malware reaches out to two IP lookup sites:
http://freegeoip[dot]net/xml/
http://api.ipify[dot]org/
These requests used a hard-coded user-agent:
The information returned by these sites is parsed to determine the user's geographic location.
The sample requests privilege escalation from the user, and falls back on modified behavior in the event it is declined:
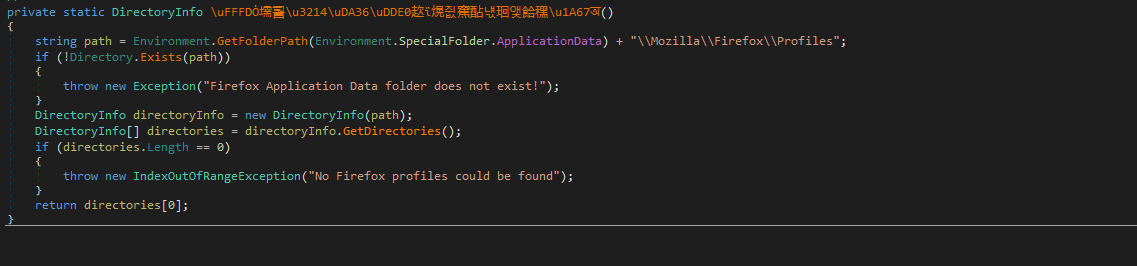
The sample moves on to harvesting cookie and stored account information from major browsers including Firefox, Opera and Chrome:
The sample sets up a key and mouse logger, output of which is stored in files in the user's AppData directory. In addition, the malware captures video frames from the victims webcam, if present:
The malware configures a reverse proxy, presumably for intercepting the victim's network activity and potentially to enable C&C.
The malware also adds an SSH key to the registry, using the user name "valueSafe" and password "text2":
The malware contains an encryption and decryption routine. It seems that many of the strings contained in the sample are encrypted and base64 encoded. I am operating on the assumption that these probably contain URLs/IP Addresses that may be exposed during dynamic analysis. It is also likely that the output of the loggers and webcam captures would be stored in encrypted files locally until they are retreived by or sent to the attacker.
The comprehensive information gathering and multiple vectors for data collection and remote access make it obvious this sample is spyware. The brevity of my static analysis prevented me from identifying reliable network indicators for this malware. I intend to perform more in-depth analysis including dynamic analysis in the near future.